ARP (Address Resolution Protocol) allows devices on a network to communicate seamlessly by mapping IP addresses to physical MAC addresses. This protocol is essential for data transmission in local networks and for efficient connections between devices.
What is Address Resolution Protocol (ARP)?
Address Resolution Protocol (ARP) is a fundamental protocol in networking that plays a key role in the communication between devices within a local network. In simple terms, ARP is used to map an IP address (used for identifying devices at the network layer) to a physical MAC address (used for communication at the data link layer). This mapping is essential because devices need both the IP address and MAC address to correctly send and receive data within a network.
Without ARP, the process of identifying devices in a network would be much more complicated. Whenever a device wants to communicate with another device, it checks its ARP cache to see if it already has a mapping for the IP address. If it doesn’t, it will send an ARP request to identify the MAC address associated with that IP, allowing the devices to establish a direct line of communication.
The History of ARP
The Address Resolution Protocol (ARP) was introduced in the early 1980s as part of the development of the IPv4 protocol suite, a key component of the Internet Protocol (IP) stack. ARP was designed to solve a basic problem that emerged as computer networks became more sophisticated: how to translate IP addresses into physical (MAC) addresses on a local network.
Originally, ARP was developed to enable devices in a shared network, such as Ethernet, to communicate with each other by efficiently mapping IP addresses to the physical hardware addresses used in data transfer. This protocol became foundational as the use of local area networks (LANs) grew, allowing devices to communicate smoothly in a network without requiring users to manually configure these mappings.
Over the years, ARP has remained largely unchanged due to its simplicity and effectiveness in addressing IP-to-MAC resolution. It has since become a core part of the IP networking suite and is essential in many network environments. However, with advancements in network security, ARP has also become a target for certain types of attacks, which are explored later in this article.
What ARP Does and How It Works
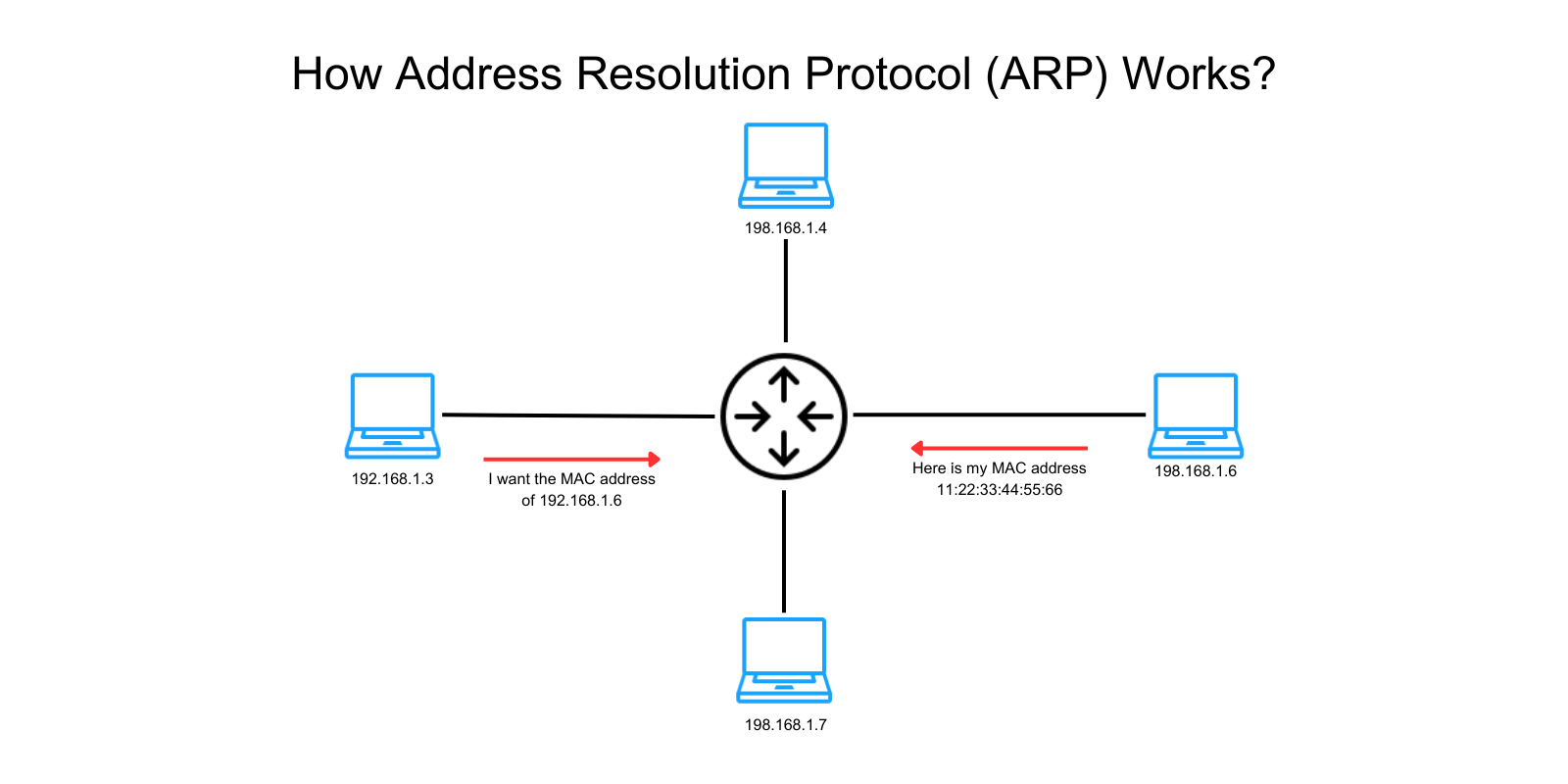
The Address Resolution Protocol (ARP) plays a vital role in enabling communication between devices on a local network by mapping IP addresses to physical MAC addresses. Here’s a breakdown of how ARP functions:
-
ARP Requests: When a device (let’s say Device A) wants to communicate with another device (Device B) on the same network, it needs to know Device B’s MAC address. If Device A only knows Device B’s IP address, it will broadcast an ARP request on the network, asking, “Who has this IP address?” This request is sent to all devices on the local network.
-
ARP Responses: When Device B receives the ARP request, it recognizes its own IP address and replies directly to Device A with its MAC address. Device A then receives this response and records the IP-MAC address pair in its ARP cache (a temporary storage used to remember recently resolved addresses). This way, Device A doesn’t need to ask again if it needs to communicate with Device B in the near future.
-
ARP Cache: The ARP cache is a table maintained by each device that stores recently resolved IP-to-MAC mappings. This cache helps reduce the number of ARP requests, optimizing network performance. Entries in the ARP cache are only kept for a limited time and are cleared periodically to ensure that any changes in the network (such as new devices or address reassignments) are accounted for.
ARP is a straightforward protocol, but it’s essential for efficient network communication. By allowing devices to discover each other’s MAC addresses, ARP ensures smooth data transfer within a local network without the need for manual configuration.
ARP from a Cybersecurity Perspective
From a cybersecurity perspective, ARP has both strengths and vulnerabilities. While it provides essential functionality in IP networking, its simplicity also leaves it open to certain types of attacks. Because ARP was designed without built-in security mechanisms, attackers can exploit it to intercept, modify, or redirect network traffic.
One significant vulnerability is ARP’s trust-based nature—devices on a local network automatically accept ARP responses without verifying their authenticity. This lack of verification creates an opportunity for malicious actors to perform attacks, such as ARP spoofing, which can lead to more advanced cyber threats, including Man-in-the-Middle (MITM) attacks.
Cybersecurity professionals consider ARP spoofing a serious threat, as it can compromise network confidentiality and integrity. To counter these vulnerabilities, networks often use additional security measures like ARP inspection, MAC address filtering, and VLAN segmentation to restrict traffic and verify ARP communications. While ARP remains a crucial part of network infrastructure, understanding its risks is essential to securing any network environment.
ARP Spoofing
ARP spoofing (also known as ARP poisoning) is a type of cyberattack in which an attacker sends false ARP messages onto a local network. The goal is to associate the attacker’s MAC address with the IP address of another device (such as the gateway or a victim’s computer), effectively redirecting traffic meant for that device to the attacker’s machine.
Once the attacker’s device is positioned between two communicating devices, they can intercept, monitor, or modify the data being exchanged. This makes ARP spoofing a significant security threat, particularly for attacks like Man-in-the-Middle (MITM), where attackers can eavesdrop on or manipulate the communication between two parties.
ARP spoofing can also be used in denial-of-service (DoS) attacks by redirecting traffic to non-existent devices, causing network disruptions. Attackers often rely on ARP spoofing because it is easy to execute and doesn’t require physical access to the network, making it a popular attack method in both public and private networks.
To prevent ARP spoofing, network administrators can implement security measures such as dynamic ARP inspection (DAI), static ARP entries, or encryption protocols that protect data in transit. Detecting ARP spoofing requires monitoring network traffic for unusual ARP messages or inconsistencies in the ARP cache.
Man-in-the-Middle (MITM) Attack
A Man-in-the-Middle (MITM) attack is a type of cyberattack where an attacker secretly intercepts and possibly alters the communication between two parties without their knowledge. In the context of ARP, a MITM attack is often carried out using ARP spoofing. By poisoning the ARP cache of devices on a local network, the attacker positions themselves between two devices, such as a user and their gateway, enabling them to intercept and manipulate the data being exchanged.
MITM attacks can be used to steal sensitive information, such as login credentials, credit card numbers, or other personal data. Additionally, attackers may alter the content of communications, inject malicious code, or redirect victims to fake websites designed to steal information or install malware.
These attacks are particularly dangerous in unsecured networks, such as public Wi-Fi, where encryption may not be used, making it easier for attackers to observe and modify network traffic. Even in more secure networks, MITM attacks can be successful if proper security measures are not in place.
To protect against MITM attacks, encryption protocols like HTTPS, SSH, and VPNs should be used to ensure that data remains secure even if intercepted. Additionally, using security features like DNSSEC, certificate pinning, and mutual authentication can help mitigate the risk of MITM attacks by verifying the integrity and authenticity of the parties involved in communication.
Don’t forget to share this post if you found it helpful!